.
Part 7: Wireless Networks
This part of the project/course introduced me to wireless network penetration testing. I learned about the things to look for during a wireless pentest assessment, how to set up a wireless pentesting lab, and how to capture and crack WPA2 PSK passwords.
Introduction
Although other wireless protocols and protocol modes exist, this project/course focuses specifically only on WPA2 PSK. The wireless attack demonstrated in this part of the project/course requires a special external wireless card that supports monitor mode. Since I do own such a card, I didn’t get a chance to follow along during the demonstration of the attack. Nonetheless, I will explain and show the process of how the attack is carried out. Very soon, I plan on buying an appropriate wireless card for pentesting purposes so that I can replicate the attack shown here (as well as other attacks outside of the scope of this project/course).
Exploiting WPA2
// What is WPA2?
WPA2 (Wi-Fi Protected Access 2) is a wireless security protocol used to secure wireless computer networks by providing encryption and authentication mechanisms, ensuring secure communication between devices and preventing unauthorized access to the network.
WPA2 includes two modes of operation: WPA2 PSK (Wi-Fi Protected Access 2 Pre-Shared Key), which is the mode that everyone’s home router typically uses, and WPA2 Enterprise, which is the mode that large corporations use.
// The Goals of a Wireless Pentest Assessment
The goals of a wireless network penetration test are to evaluate the strength of protocols like WPA2 PSK, review nearby wireless access points to check for any rogue wireless devices in the network, assess the security of guest accounts/networks if they are enabled (e.g., checking for: guest accounts without set passwords, guest accounts with default/weak passwords, guest accounts without enforced network segmentation), and test the network’s overall network segmentation (e.g., can you: pivot to other networks that you shouldn’t have access to, access resources through the main or guest wifi networks without authorization).
The demonstration shown here will only focus on the first goal: evaluating the strength of WPA2 PSK.
// Wireless Lab Setup
The tools used for demonstration are: an external wireless card (Alfa AWUD036NH), a router (TP Link AC2300 Wireless), and a laptop (connected to the router’s Wi-Fi network).
The Alfa wireless card is a beefy wireless card that can listen to and inject packets on a wireless network, without even being authenticated to it. The wireless cards that are built into the typical computer don’t have these capabilities, which is why such an external wireless card is needed for pentesting.
// Capturing and Cracking WPA2 PSK Passwords
The demonstration shown here will focus on showing how easily a WPA2 PSK network can be compromised if it uses a weak Wi-Fi password. The password will be captured and cracked by abusing the four-way handshake process. The four-way handshake is a cryptographic process in WPA2 PSK that establishes a secure connection between a client device and a wireless access point by authenticating the client’s possession of the correct pre-shared key (PSK; the Wi-Fi network’s password) and deriving encryption keys for securing the wireless communication. During the four-way handshake, this PSK will be captured in encrypted form and then cracked.
Let’s see how this attack works:
First, you’re going to want to plug in your external wireless card into your Kali machine. Then you want to run iwconfig to make sure your Kali machine is recognizing and using the wireless card by checking if the wlan0 wireless network interface is up, followed by airmon-ng check kill to kill any processes that might interfere with the attack process, and lastly airmon-ng start wlan0 to start monitor mode on the external wireless card. After doing this, your wlan0 interface should change to wlan0mon.
Then use airodump-ng wlan0mon to dump out all local wifi networks, find your target SSID, and take note of its BSSID and channel number:

In this case, our target SSID is TP-Link_0074, as shown above. Now that we have the BSSID and channel number of our target SSID, we can now target it for precise packet sniffing using airodump-ng -c <channel> --bssid <bssid> -w capture <capture file>. This command will only sniff traffic from the target network, excluding the traffic from all other networks. The capture file, which we can specify the name of, will be later used to store the PSK once it is captured.
Let’s see what running that command looks like:
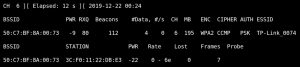
Running this command will show all computers connected to the target SSID under the STATION column. In this case, only 1 computer is connected to our target SSID. At this point, the next time a handshake process happens in the network, we will capture the encrypted network PSK, which we can then try to crack. We can sit and wait here for a handshake to come through or we can speed up the process by doing an injected deauthorization attack, which deauthenticates somebody (kicks them off) from the wireless network for one second. After the one second is up, their computer will automatically authenticate with the network again. This reauthentication process triggers a handshake.
You can run the deauth attack by running: aireplay-ng -0 -a <bssid> -c <target station> wlan0mon. Let’s kick off the sole computer connected to our target SSID:
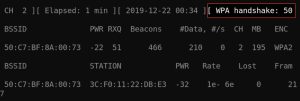
As you can see, after kicking off the computer, airodump-ng shows a message confirming that a handshake occurred. The PSK should now be stored in your capture file.
From here, we can now try to crack the PSK by running aircrack-ng -w <wordlist> -b <bssid> <.cap file>:
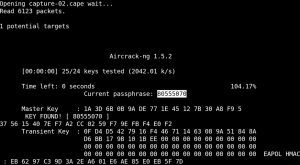
{$}
<contact_me>
Fill out the form below to reach out to me!